Web3 Infra Series | The Role of Identity in Web3 Infrastructure
Published on May 30, 2025

Online identity, ever since the early internet, has revolved around
account-based systems like e-mails, usernames, passwords, and ID
numbers. These are mechanisms, essentially, that prove you’re allowed
in.
Your Google login gives you access to Gmail, YouTube, and Google
Drive, but it doesn’t work on Apple services, Facebook, or government
platforms. Identifiers like these were novel at the time, but were
really built for isolated, walled-garden platforms, so they don’t
carry over or adapt outside of the system that issued them.
Most people today rely heavily on platforms like Google or Apple to
manage their logins, but that kind of convenience comes with the cost
of control, as these companies decide exactly how your identity is
issued, what data gets shared, and which apps are allowed access.
The 2018 Cambridge Analytica scandal exposed exactly how much control
these platforms hold, everything from user identities, behavior
patterns, and preferences was mined, packaged, and sold to the highest
bidder without consent. This also wasn’t a bug, it was the business
model. Web3 identity is a structural answer to that problem, giving
users custody over their credentials instead of surrendering them at
the door.
Uptick is designed to avoid this kind of lock-in, using modular,
cross-chain infrastructure that keeps identity portable. The old model
creates unnecessary friction, but programmable identity is beginning
to show glimmers of promise, and that’s because it isn’t simply a
digital version of a passport or a repackaged KYC, it’s a totally
modular identity system that connects user roles, access logic, and
credential data across protocols.
All without needing a central authority to manage it.
That last part completely changes how access works, how compliance can
be automated, and how users interact across different ecosystems. In
Web3, identity becomes something you carry with you in a sovereign
way, not something issued and owned by platforms.

When Equifax lost the data of 147 million people in 2017, including
social security numbers and financial records, it was a big reminder
that centralizing identity, along with friction, creates systemic
risk. In contrast, decentralized identity removes that single point of
failure entirely.
Decentralized identity is a programmable layer that defines how users
move, what they can access, and how they’re trusted.
For a modular Web3 stack to work, identity needs to be portable,
verifiable, and privacy-minded. That makes it infrastructure, not a
simple convenience layer or front-end feature, and identity actually
has the potential to shape how the system works, beyond just letting
users sign in.
Decentralized identity is built on three core components: identifiers,
credentials, and proofs.
Many still think of Web3 identity as repackaged KYC, but its real
value lies in its flexibility and the layered infrastructure that
supports it. Decentralized identifiers act as sovereign containers for
credentials, attributes, and proofs, which can be issued, updated, or
revoked both on-chain and off-chain.
At the base is the DID, which is a persistent anchor for identity.

On top of that are verifiable credentials, attaching claims like age,
certification, membership, or qualifications. These can be issued by
institutions, DAOs, apps, or other users, and used to prove identity
or eligibility without disclosing unnecessary data.
Above that sit proofs, which verify the claims without revealing the
underlying data.
This layered model gives identity the huge flexibility that’s needed
to adapt across use cases, from content access and event ticketing to
lending, governance, and enterprise integrations. It then becomes more
about building a system that fits different contexts, rather than your
average global login. Something that supports composability, and works
across both permissionless and regulated environments.
This is what makes programmable trust possible.

Uptick’s DID system is W3C-compliant and based on Iden3 by Privado,
which is designed with portability in mind, allowing users to carry
verified attributes like age, residency, or contributor status across
platforms without exposing personal data, all while adapting to the
logic of the application or asset they interact with.
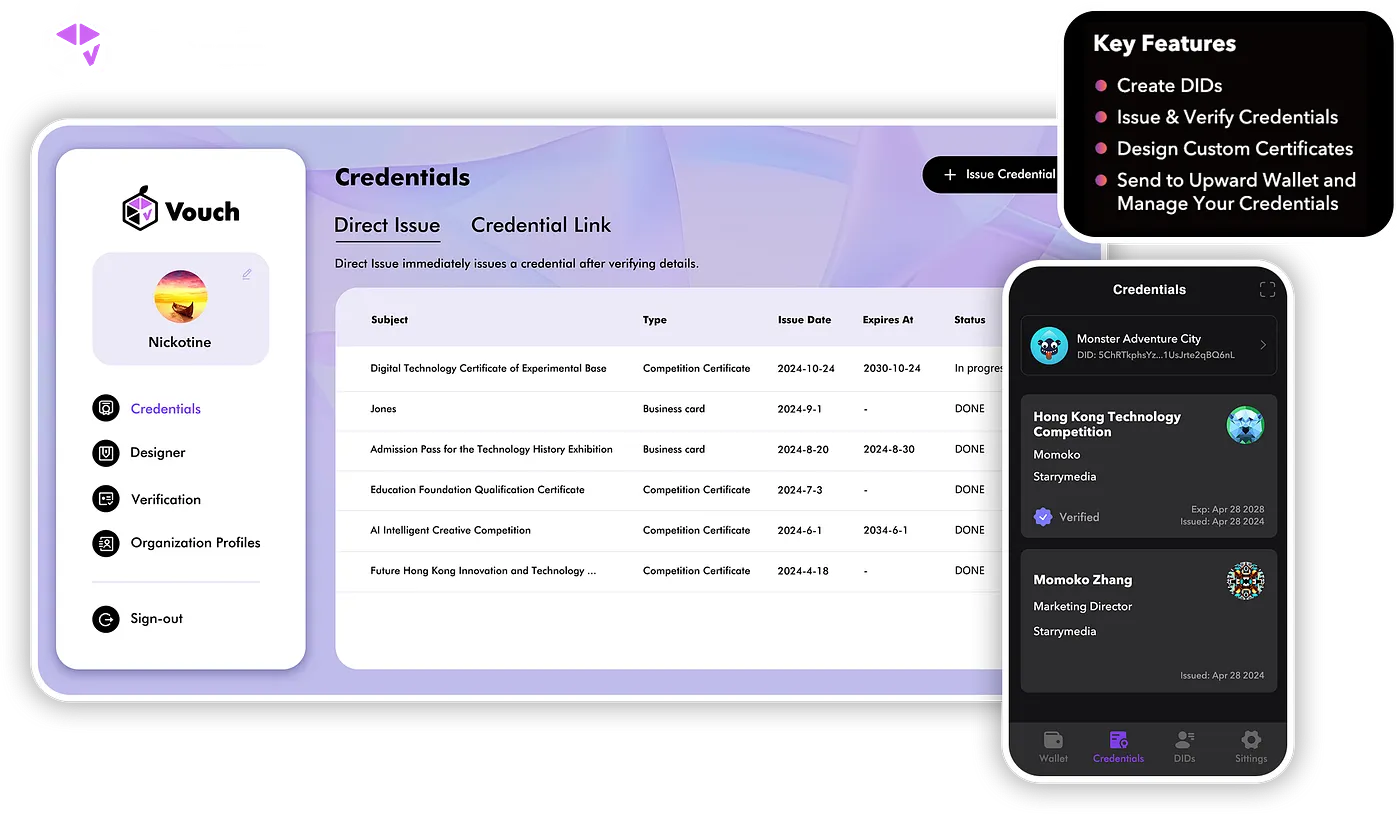
Credentials like this can already be issued and managed directly using
Vouch
, Uptick’s live DID and verifiable credential platform. Vouch handles
everything from DID creation to credential design and issuance, with
support for both direct DID-based distribution and claimable links via
QR codes. It also supports revocation and expiry, allowing credentials
to adapt as user roles or conditions change.

In comparison to the traditional Web2 model, platforms like Vouch
shift identity from something completely fixed to something modular,
and something that can adapt dynamically. Instead of starting over in
every application, users should be able to carry their identity with
them.
Composability is the core concept.
Issuers decide what to share, when, and with whom. One credential
might prove age, whereas another might unlock access to a private NFT
drop, or another might confirm DAO membership.
Each credential is context-bound and evolves as users interact with
asset conditions, application permissions, or governance logic.
Identity isn’t a single profile, it’s made of smaller parts that move
together.
DIDs, credentials, and proofs each serve a role, which can be issued
separately, revealed selectively, and combined when needed. This
unlocks a wide range of use cases, everything from social reputation,
compliance logic, on-chain credentials, and role-based access, which
all rely on the same infrastructure.
Identity becomes the connective layer between users and apps, adding
context to interactions and helping systems recognize behavior instead
of relying on basic access controls. In essence, the more interactions
that tie back to verifiable identity, the more useful and
interoperable the network becomes.

In Web2, identity is tied to accounts and controlled by platforms.
You log in with Google, Facebook, or an email, and the platform holds
your data, sets the permissions, and essentially shapes the outcome.
That worked in closed environments, but it doesn’t scale across
ecosystems that rely on shared context and distributed trust.

This model means that users have to rebuild trust from scratch every
time they use a new app. Every platform builds its own silo, with no
way to connect identity or history between them, so trust resets each
time a user moves. That turns it into a business asset instead of a
user utility, which also slows things down as data cannot move with
the user.
Web3 infrastructure can’t just copy the same model.
As we’ve prefaced throughout this article, identity should be modular,
portable, and verifiable, without relying on a middle layer, and
should align with permissionless access, transparency, and user
control.
Simply rebuilding login systems on-chain misses the point. Otherwise,
we end up with the same problems, just in a shinier Web3 format.

Decentralized identity reverses the structure, because users manage
their credentials, and applications verify them, but don’t actually
store them, which builds trusted interactions over time. Reputation
can then span ecosystems without being locked to one provider, and
identity becomes part of the stack, and not a service layered on top.
Identity is often seen as a frontend concern when it comes to wallet
integrations, access flows, or login methods, but identity sits much
deeper in the stack, enabling asset-level permissioning, role-based
governance, delegated authority, and reputation-weighted logic.
This defines who can take action, under what conditions, and why it’s
allowed. Decentralized identity allows smart contracts to enforce
compliance without relying on centralized oversight, making token
access possible without storing user data.
It also connects real-world credentials to digital interactions
without destroying privacy or decentralization. With this, identity
becomes a foundational layer for programmable systems that enforce
logic at runtime.

Uptick integrates DID modules at the protocol level, which means that
identity is part of the core infrastructure, and every identity is
designed to connect directly with asset logic, permissioning systems,
and application layers, so it’s treated as a carefully considered
design component.
Each DID anchors a set of verifiable credentials, which can then
define asset access, trigger compliance checks, or support reputation
systems across applications. We can then have the ability to enforce
credential rules at the asset level, where one token might require
proof of residency, or another might allow access only for verified
contributors.
Each asset can define its own conditions, applied contextually at the
point of interaction, avoiding bottlenecks and allowing for
permissioning without affecting the flexibility of it all.

An RWA might require proof of residency, and another might need
investor accreditation, or a DAO vote might be limited to verified
contributors. Asset-specific rules provide precision but without
creating central bottlenecks.
These are modular credential checks, applied at the point of
interaction.
Uptick’s DID structure is built to function as a permission layer that
moves with the asset, across its entire lifecycle. Verifiable
credentials stay attached throughout, so ownership and eligibility can
be checked anywhere, without central coordination or resets.
With cross-chain functionality, and built-in support for zero
knowledge proofs that allows users to verify claims without revealing
personal data, this kind of infrastructure design gives identity
portability without lock-in, and compliance without surveillance.

Reputation is identity over time, and it reflects actions,
verifications, and relationships that give an identity weight. In
Homeric tradition, this was known as kleos, glory earned through
deeds, not titles. Web3, in a sense, builds on the same idea, turning
behavior into a persistent signal that systems can recognize.
Web3 reputation is starting to replace credit scores, trust ratings,
and static user profiles without requiring centralized storage or
fixed identities, which allows for distributed trust that grows
through participation. This also unlocks new models for credit
delegation, DAO governance, and creator incentives, where one could
have a contributor badge, a history of verified deliveries, or a trail
of credentials that shape how users interact with systems.
Access, risk levels, and voting power can all adjust dynamically based
on reputation inputs.
Reputation also provides sybil resistance without needing real names,
because it allows systems to assess users based on behavior instead of
identity disclosure, which is essential for any open network that
wants to stay permissionless, as it filters out spam and fraud, with
trust becoming contextual and earned, not assigned.

Uptick is building a model where reputation exists as a portable,
verifiable layer, earned through participation and referenced directly
in application logic alongside asset and identity layers.
Decentralized CRM (DCRM) can track verified actions, contribution
history, and contextual feedback without aggregating user data in a
central service, so applications can recognize behavior without
needing personal details or permanent identifiers.
This means that every action can contribute to a broader profile
without requiring aggregation by a central entity.

A working identity system should prioritize privacy.
That doesn’t mean hiding everything in sight, it just means giving
users control over what they reveal and when. This becomes especially
important when credentials include aspects such as legal status,
medical history, or financial information, the kind of data that can
be misused if exposed.
Without privacy, composability loses its value.
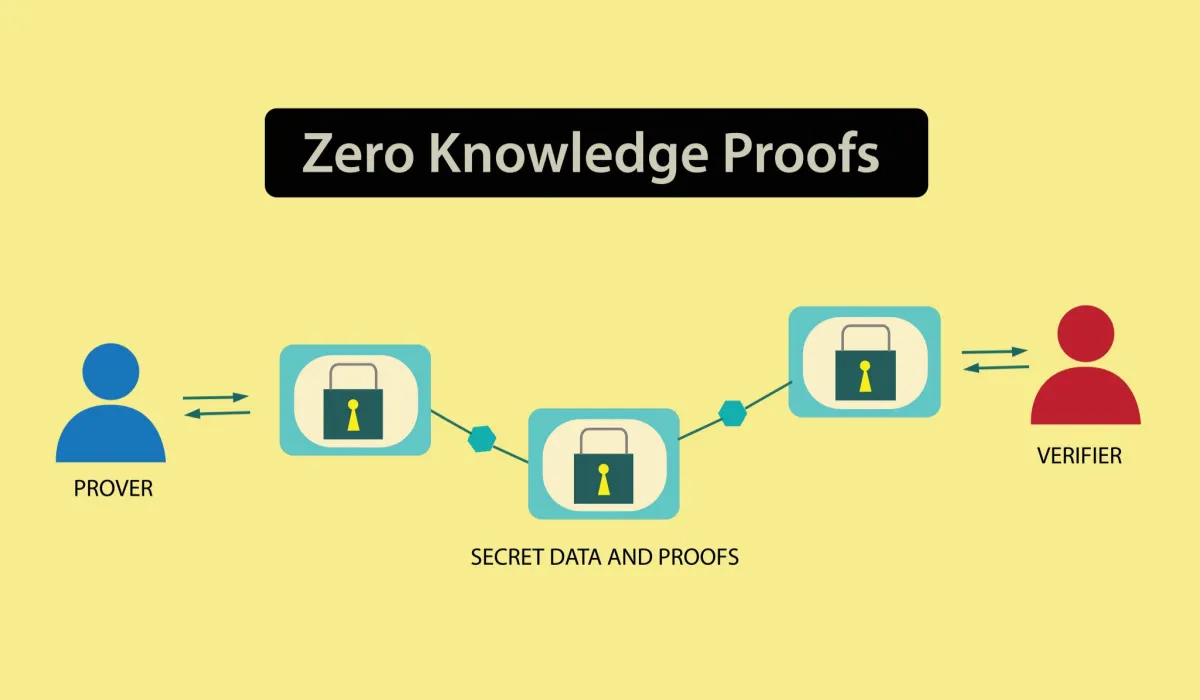
Zero knowledge proofs are enforced at the protocol level, allowing
users to prove eligibility without revealing the underlying data.
Selective disclosure is about partial verification without full
access, and encrypted metadata keeps credentials private, even when
used on public networks.
This creates a secure base for programmable trust, giving users
control over what’s shown, when, and to whom. Eligibility replaces
identity, so you don’t need a name or passport number to mint a token
or vote in a DAO, only proof that the condition is met.
That’s what decentralized identity enables, validation without
exposure.

Privacy-preserving identity is what makes regulated DeFi, enterprise
governance, and institutional asset issuance possible, and without it,
Web3 remains rather limited or just slides back toward centralization.
With it though, entire categories of users and use cases can exist
on-chain and operate across borders.
Vouch, Uptick’s credential platform, supports selective disclosure,
expiration, and revocation, keeping credentials usable and relevant
across systems. It also supports zero knowledge-proof issuance paths
as part of its ongoing roadmap. This allows credential holders to
selectively reveal data when interacting with dApps, DAOs, or asset
systems, all from a single DID anchored on Uptick infrastructure and
then conveniently stored in the Upward Wallet.
Essentially, it functions as a secure credential vault with interfaces
for ZK-based interactions during dApp or DAO use.

One might think that decentralized identity is just a user primitive,
but it’s actually a system-level component, and in a modular Web3
stack, identity is the thing that connects everything together.
Decentralized identity allows open systems to apply rules.
Access control, asset management, compliance, governance, and
community engagement all rely on it. Identity links modules, products,
and ecosystems, giving systems context, continuity, and precision.
This gives users consistency across applications, and developers can
define permission logic without building barriers. Institutions gain a
way into Web3 without losing regulatory clarity or usability, so
identity makes structured participation possible without requiring new
trust models for every single app.
Uptick treats identity as a core infrastructure component, working
alongside the asset lifecycle engine, data services, and governance
modules. Identity gives assets meaning, assets define interactions,
and data connects both. When these parts are composable,
infrastructure becomes so much more adaptable, and that’s what allows
it to support more than just rudimentary transactions.

Identity is moving away from account-based systems and toward
verifiable, composable credentials. With this shift, trust comes from
behavior rather than platform assignment, and interactions become
contextual, private by default, and compatible across networks.
Identity then sits alongside tokens, wallets, and data feeds as a core
layer of the Web3 stack.
This shift changes how developers approach access control, so instead
of rebuilding identity logic for every new application, they can
define permission rules directly at the asset or app level, using
credentials that move with the user. However, supporting this model
requires infrastructure that treats identity as part of the stack.
Uptick provides that foundation, as the protocol includes a DID
system, modular credential logic, and built-in support for zero
knowledge-based verification, all integrated with asset logic, access
control, and governance modules. Uptick’s identity system supports
selective disclosure, and platforms like Vouch, already integrated
within the Uptick stack, allow these credentials to be issued once and
used across different systems, enabling developers to enforce
permission rules without managing user data directly.
Credentials are then able to prove eligibility without exposing the
underlying data, and since zero knowledge support is part of the
architecture, users can meet conditions without revealing personal
information. This enables everything from private voting, to regulated
asset access, to compliance checks within open systems.
It’s a long road ahead, but as identity continues to evolve, it is
becoming a foundational layer that defines trust, access, and
coordination across networked systems, one that is programmable and
portable in design, and built to keep control in the hands of the
user.























